Security Providers
A security provider is used to override the default security behavior when using early bound security. It gives the implementor the ability to indicate the access control for each indexed document, along with the current users group membership.
The Perceptive Search Security Model is extensible allowing you to map non-Windows based security systems into the early binding module.
The system currently supports extension via Script, however this will be extended to support .net, DLL, com and Java modules in the near future.
There are several use-cases to consider when implementing the custom connectors:
- The system uses Windows to authenticate the user (by default), with:
- the content source using Windows (Active Directory) groups not stored in NTFS
- the content source using custom groups, independent of those stored in Windows/Active Directory
- The system does not use Windows to authenticate the user (Lotus Notes for example)
Windows User, Built-in Windows Groups
This scenario covers systems that use Windows to both authenticate the user and Windows users/groups to control permissions to resources, but the security information is not stored in the NTFS file system. An example of this maybe an SQL database.
For this option, all that is needed to be implemented is the RequestSecurity function that returns the permissions for the requested resources. This will be called once for each document at indexing time.
The sample below demonstrates programmatically setting permissions based on the folder, overriding the NTFS permissions.
function RequestSecurity(Request, Response) if InStr(Request.Filename, "/top-secret/") > 0 then Response.AddSID "GroupTopSecret", True elseif InStr(Request.Filename, "/classified/") > 0 then Response.AddSID "GroupClassified", True else Response.AddSID "Everyone", True end if end function
Windows User, Custom Groups
This scenario covers systems that use Windows to authenticate the user, but use a different user/group mechanism than standard Windows/Active Directory. An example of this is an ASP.NET website that uses a database stored, role based security scheme.
For this option, we need to implement both RequestSecurity to return the permissions of the resource; and RequestUserGroups to return the list of groups that the user is a member of.
Consider the following database schema:
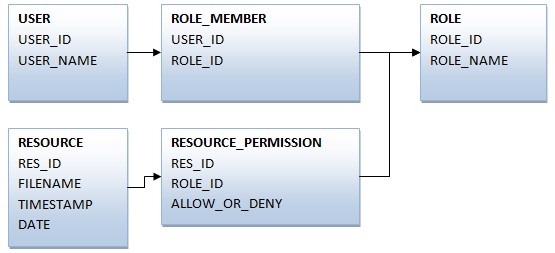
In the above schema:
- the USER_NAME column contains the user's Windows username.
- a user can belong to zero or more roles.
- a resource can contain zero or more permissions including or excluding specific roles.
- this sample assumes the RESOURCE table has been indexed.
function RequestSecurity(Request, Response) Set RecordSet = ExecuteSQL(" SELECT ROLE.ROLE_NAME, RESOURCE_PERMISSION.ALLOW_OR_DENY FROM RESOURCE_PERMISSION JOIN ROLE ON ROLE.ROLE_ID = RESOURCE_PERMISSION.ROLE_ID JOIN RESOURCE ON RESOURCE.RES_ID = RESOURCE_PERMISSION.RES_ID WHERE RESOURCE.FILENAME = ?", Request.Filename) for each Record in RecordSet Response.Add Record("ROLE_NAME"), Record("ALLOW_OR_DENY") next end function function RequestUserGroups(UserName, Response) Set RecordSet = ExecuteSQL(" SELECT ROLE.ROLE_NAME FROM ROLE JOIN ROLE_MEMBER ON ROLE_MEMBER.ROLE_ID = ROLE.ROLE_ID JOIN USER ON USER.USER_ID = ROLE_MEMBER.USER_ID WHERE USER.USER_NAME = ?", Username) for each Record in RecordSet Response.Add Record("ROLE_NAME") Next end function
Non Windows User based Security System
At this time, Perceptive Search supports one user authentication system to be installed on a web site at a time. A lot of systems use Windows as their user authentication system (File System, SharePoint, TRIM etc), so there is no special requirement to search these systems together.
For other systems, it's recommended that a mapping be applied between the Windows username and the remote system username. This becomes easier if the organization has a username policy that enforces that the same username be is used for both Windows and the other systems (i.e. logon to Windows as Joe.Smith and Lotus as Joe.Smith).
As with "Windows User, Custom Groups", you will need to implement both RequestSecurity and RequestUserGroups.
To create a security provider script, you need to implement some of the functions below:
Sub RequestSecurity(Request, Response)
RequestSecurity is called during indexing allow you to provide the access control information for the requested document.
Parameters
Request
Contains information about the document whose security is being
requested, properties include:
| Request.Filename | returns the filename of the document being requested (as return from ScanFirst/ScanNext). |
| Request.IndexPath | returns the path to the index being updated. |
| Request.Properties | returns a collection of NTFS file system properties (Windows only). |
| Request.Script | returns the name of the script currently executing. |
| Request.Size | returns the size of the file on disk, if available. |
| Request.TimeStamp | returns the timestamp on disk, if available. |
Response
Populate the response object with the security for the document. Response
properties/methods are:
| Response.Add(UserOrGroupID, AllowOrDeny) | Adds the name and access specified to the security collection for this document. |
| Response.AddSID(UserOrGroup, AllowOrDeny) | Adds the SID of the group or user named to the security collection for this document. |
Function RequestUserGroups(Username, Response)
Requested at search time, allows you to return the groups that the searching user is a member of.
Parameters
Username - The name of the searching user
Response
Populate the response object with the security for the document. Response
properties/methods are:
| Response.Add(UserOrGroupID) | Adds the name to the security collection for this user. |
| Response.AddSID(UserOrGroup) | Adds the SID of the group or user named to the security collection for this user. |